Learning from the COSMOS Bank Breach!
By MYBRANDBOOK

COSMOS Bank, a 112-year old cooperative bank in India and the second largest in the country was being hacked and crores were siphoned off. As per reports, the fraudulent transactions were carried out on August 11 and August 13 and the malware attack by the hackers originated in Canada.
In the first attack on August 11, using stolen card details, approximately Rs. 78 crore was withdrawn in transactions in 28 countries. This included around 12,000 Visa card transactions. On the same day, approximately, Rs 2.5 crore was withdrawn through 2,800 debit card transactions in India at various locations.
On August 13, the hackers transferred Rs 13.94 crore into an account in the Hang Seng Bank in Hong Kong by initiating a SWIFT transaction.
"In two days, hackers withdrew a total Rs. 78 crore from various ATMs in 28 countries, including Canada, Hong Kong and a few ATMs in India, and another Rs. 2.5 crore were taken out within India," Cosmos Bank chairman Milind Kale said. "It was observed that unusual repeated transactions were taking place through Visa and Rupay cards used at various ATMs for nearly two hours."
As per the Bank officials there were 2 main reasons for the hack -
Malware attack on a switch, which was operative for payments gateways - The incident came to light on August 11, Saturday, when unusual, repeated transactions were taking place through ATM Visa and Rupay cards for nearly two hours. As per the report, there was a malware attack on a switch which was operative as a payment gateway for VISA and Rupay cards.
Core banking system (CBS) of the bank usually receives debit card payment requests via 'switching system', but during this malware attack, a proxy switch was created and all the fraudulent payment approvals were passed by this proxy switching system.
Cloning of Bank’s Debit Cards used for Fraudulent Transactions - Fake debit cards were used for the transactions at ATMs. Malware has created the proxy switch, and fraudulent payments were approved by this proxy switching system without reaching to the bank’s Core Banking System (CBS).
Technical details
After making adjustments to the target account balances to enable withdrawals, MC was then likely used in fake “*on-us,” foreign-to-EFT, standing-in, etc. activity that enabled the malicious threat actor to authorize ATM withdrawals of over US$11.5 million in 2849 domestic (Rupay) and 12,000 international (Visa) transactions using 450 cloned (non-EMV) debit cards in 28 countries.
Using MC, attackers were likely able to send fake Transaction Reply (TRE) messages in response to Transaction Request (TRQ) messages from cardholders and terminals. As a result, the required ISO 8583 messages (an international standard for systems that exchange electronic transactions initiated by cardholders using payment cards) were never forwarded to the backend/CBS from the ATM/POS switching solution that was compromised, which enabled the malicious withdrawals and impacted the fraud detection capabilities on the banking backend.
Cosmos Bank Cyberattack–SWIFT Modality–US$2 Million Stolen
On August 13, 2018, the malicious threat actor continued the attack against Cosmos Bank by moving laterally and using the Cosmos bank’s SWIFT SAA environment LSO/RSO compromise/authentication to send three malicious MT103 to ALM Trading Limited at Hang Seng Bank in Hong Kong amounting to around US$2 million.
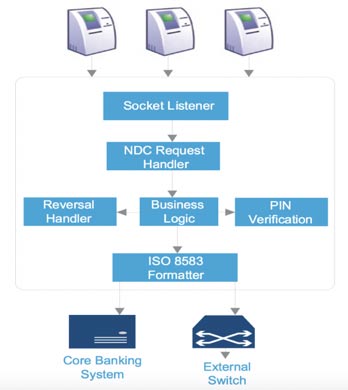
The ATM/POS banking switch that was compromised in the Cosmos Bank attack is a component that typically provides hosted ATM/POS terminal support, an interface to core banking solution (CBS) or another core financial system, and connectivity to regional, national or international networks. The primary purpose of the system is to perform transaction processing and routing decisions (see Figure 1).
In case of the Cosmos Bank attack, this was not the typical basic card-not-present (CNP), jackpotting, or blackboxing fraud. The attack was a more advanced, well-planned, and highly- coordinated operation that focused on the bank’s infrastructure, effectively bypassing the three main layers of defense per Interpol Banking/ATM attack mitigation guidance.
After analyzing COSMOS Bank breach, we have many things to learn so that these kinds of breaches can be avoided in future. Some of the key learning from the COSMOS Bank hack are as the following -
Looking in to the scale and planning of the attack, it requires a gang of hackers. It was also believed that smaller banks with less sophisticated security systems were targeted because of less sophisticated cyber security.
The FBI said these types of ATM cashouts are most common at smaller financial institutions that may not have sufficient resources dedicated to staying up to date with the latest security measures for handling payment card data.
Similar kind of attacks have happened earlier on City Union Bank where hackers disabled the City printer connected to global payments platform SWIFT on Feb. 6, 2018, preventing the bank from receiving acknowledgement messages for three fraudulent payment instructions sent that evening until the next morning.
In the case of Bangladesh Bank, hackers infected the system with malware that disabled the SWIFT. Printer. Bank officials in Dhaka initially assumed there was simply a printer problem.
Smaller financial institutions have major gaps in the CyberSecurity posture
As per the Bank, the malware attack was on the switch, which is operative for payment gateways of Visa and Rupay debit cards. By cloning the cards and using a "parallel" or proxy switch system, the hackers self-approved the transactions and withdrew over Rs 80.5 crore in about 15,000 transactions.
COSMOS Bank has not fully encrypted its payment processing network. This can allow hackers who have access to the network to divert and/or alter the response that has sent to ATM when an ATM transaction is requested. So, even if transaction is getting declined, thieves can switch it from declined to approved.
Regulatory authorities cannot overlook smaller financial institutions
Former NPCI managing director and CEO, A P Hota was of the view that the RBI has clear guidelines and if these are followed, such incidents will not happen. “There is a case that as far as security is concerned, attention is given more to commercial banks and cooperative banks have been side- lined. However, there are 9-10 cooperative banks as big as private banks and Cosmos Bank is one of them. Maybe RBI should pay special attention to large cooperative banks,” Hota told the Indian Express.
There is an urgent need to address a lack of preparedness among cooperative banks in India to mitigate cyber attacks.Banks failing to follow the security guidelines issued by the regulators like RBI causing such loss. The financial impact of a loss of brand reputation and trust after a cybersecurity incident can be significant for the bank. Because of the breach, a bank has irreparable damage to its reputation. In this connected world, the COSMOS Bank breach news spread very fast, and it has been branded as a breached Indian Bank internationally. It will impact their future operations either with their clients or partners or stakeholders. They will face difficulty in acquiring new customers, as people fear keeping their money in a breached bank which has lost crores.


Legal Battle Over IT Act Intensifies Amid Musk’s India Plans
The outcome of the legal dispute between X Corp and the Indian government c...

Wipro inks 10-year deal with Phoenix Group's ReAssure UK worth
The agreement, executed through Wipro and its 100% subsidiary,...

Centre announces that DPDP Rules nearing Finalisation by April
The government seeks to refine the rules for robust data protection, ensuri...

Home Ministry cracks down on PoS agents in digital arrest scam
Digital arrest scams are a growing cybercrime where victims are coerced or ...


Icons Of India : Arundhati Bhattacharya
Arundhati Bhattacharya serves as the Chairperson and CEO of Salesforce...

Icons Of India : NIKHIL RATHI
Co-founder & CEO of Web Werks, a global leader in Data Centers and Clo...

Icons Of India : MADHABI PURI BUCH
Madhabi Puri Buch is the first-female chairperson of India’s markets...


UIDAI - Unique Identification Authority of India
UIDAI and the Aadhaar system represent a significant milestone in Indi...

IOCL - Indian Oil Corporation Ltd.
IOCL is India’s largest oil refining and marketing company ...

ECIL - Electronics Corporation of India Limited
ECIL is distinguished by its diverse technological capabilities and it...


Indian Tech Talent Excelling The Tech World - Rajiv Ramaswami, President & CEO, Nutanix Technologies
Rajiv Ramaswami, President and CEO of Nutanix, brings over 30 years of...

Indian Tech Talent Excelling The Tech World - NIKESH ARORA, Chairman CEO - Palo Alto Networks
Nikesh Arora, the Chairman and CEO of Palo Alto Networks, is steering ...

Indian Tech Talent Excelling The Tech World - Shantanu Narayen, CEO- Adobe Systems Incorporated
Shantanu Narayen, CEO of Adobe Systems Incorporated, is renowned for h...
 of images belongs to the respective copyright holders
of images belongs to the respective copyright holders